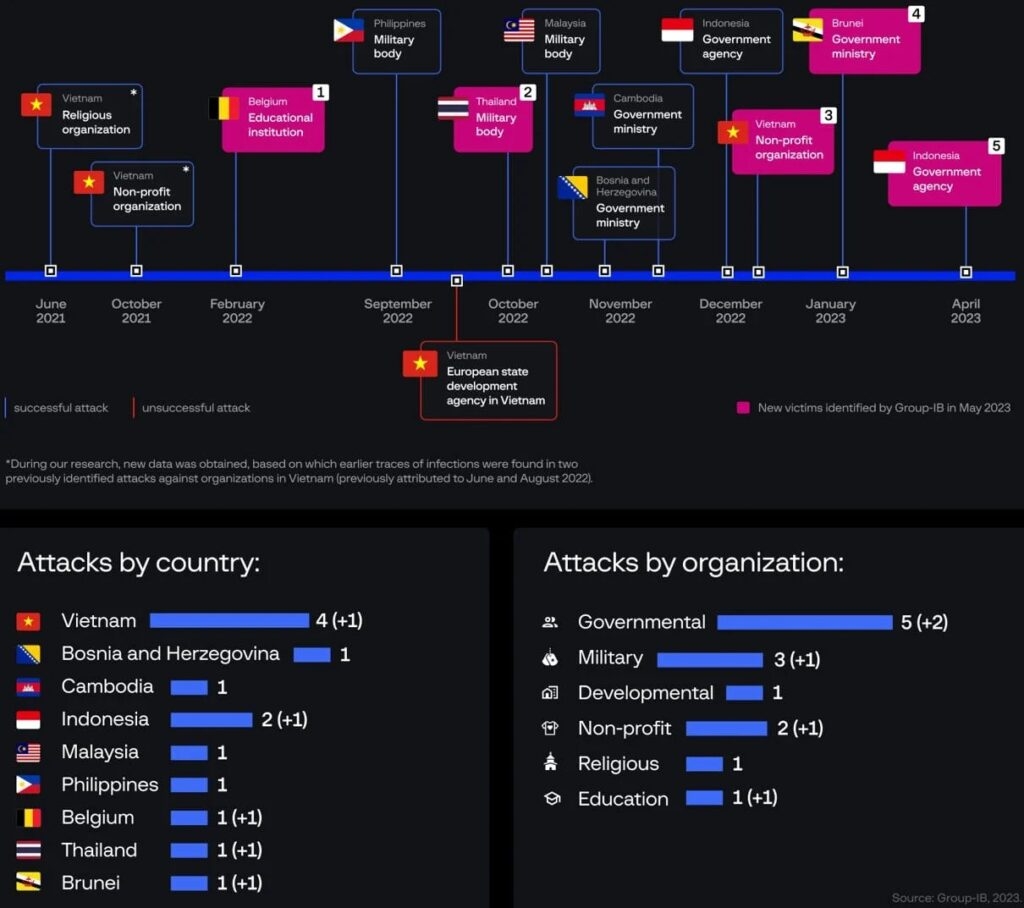
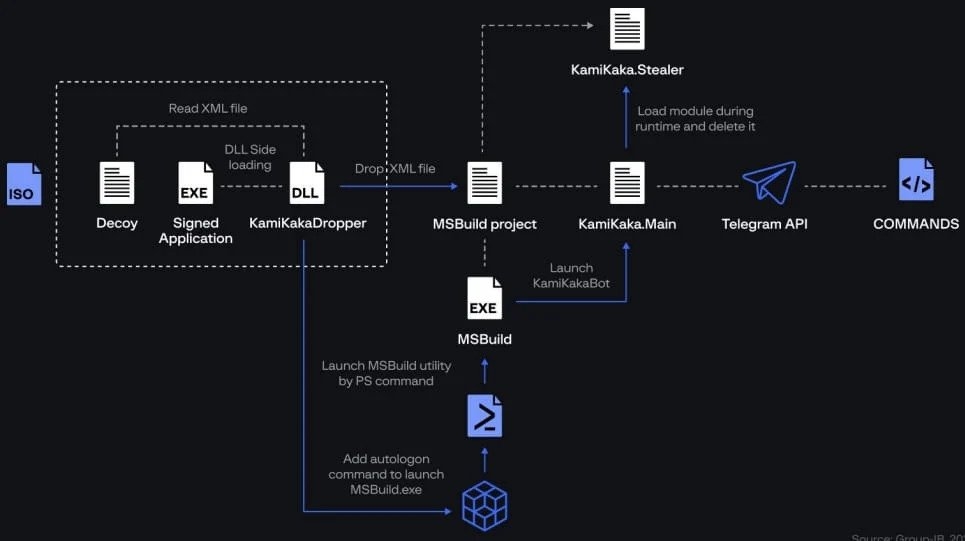
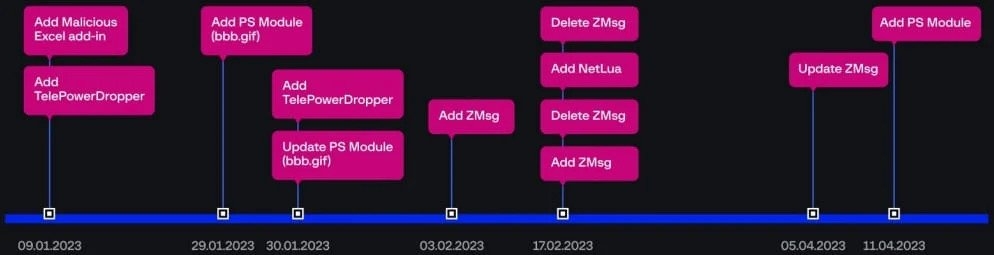
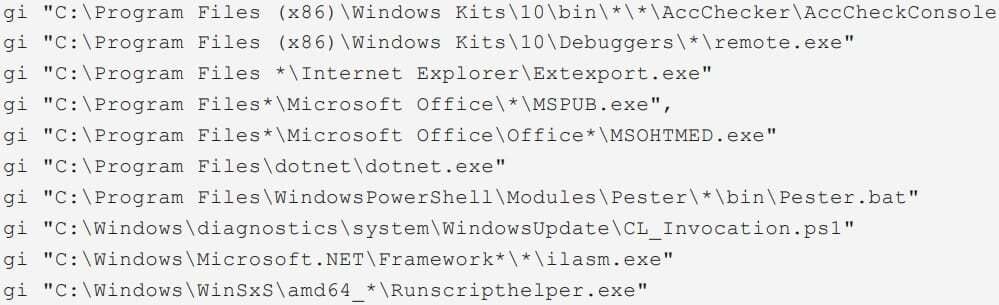
Well, in the recent attacks, the threat group displayed a revamped attack chain, executed different persistent methods, and deployed new exfiltration tools, most likely to avoid detection by separating their activity from publically available In Indicators of compromise. The researchers mention this after analyzing the previous campaign by the hacker group. The researchers found additional breaches against an educational institution in Belgium and a military space in Thailand. The Dark Pink APT is a hacker group that mainly runs campaigns on military & government agencies in the Asia Pacific regions, and it has been active since mid-2021. It was first unmasked in January 2023 by a report from Group IB. Well, even with the threat actors being exposed earlier by Group iB, the hacker group has not slowed down any bit, and as per the firm, it has spotted at least five attacks carried out by the Dark Pink APT group after writing the previous report. Read: WordPress Plugin Exploit: Massive Attacks Target Beautiful Cookie Consent Banner The Dark Pink attacks continue to depend upon the ISO archives sent via the spear phishing for the initial infection, which utilizes DLL side loading to start its signature backdoor, i.e., Tele PowerBot & KamiKakaBot. The new component is that the attackers have split the KamiKakaBot process into two parts, that is, data theft and device control. Also, it is loaded with memory, never-ending the desk. It helps to avoid detection as the antivirus software does not watch the methods that start in memory. The backdoor KamiKakaBot still targets the data stored in the web browsers and sends it to them threat actors via telegram. In addition to this, the backdoor can also download and carry out arbitrary scripts on the compromised device. The security firm found that Dark Pink uses a private GitHub repository to host extra modules downloaded by the malicious malware on the infected devices. The hackers carried out only 12 commits on the repository throughout 2023, mostly to add or upgrade the malware PowerShell scripts, ZMsg info stealer, malware droppers, and the Nethua privilege escalation tool. One of the PowerShell scripts is Censorious for malware’s material movement strategy, helping to identify and interact with SMB shares within the network. The script gets the ZIP archive from GitHub, saves it to the local directory, and then makes an LNK file on each SMB share linked to the executables in the archive When the victim opens the LNK file, the LNK file launches the malicious executables, forwarding the hack group’s multiplication all over the network and expanding its reach to more systems. Dark Pink uses PowerShell commands to carry out checks for the presence of authentic software and deployment tools on the infected system that they can exploit for their operations. The tools include “AceCheckConsole.exe, remote exe, Extexport.exe, MSPUB.exe, and MSOHTMED.exe,” which can be utilized for proxy execution, downloading the extra payloads & more. However, the company has not seen examples of these tools being exploited in attacks. The company Group IB reported that the hacker group displayed variations in its data exfiltration process and is going beyond the ZIP archive to Telegram channels. Furthermore, in some scenarios, the hackers used DropBox uploads, and in others scenarios, the group used HTTP exfiltration utilizing a temporary exploit created within Webbook.site service or Windows servers. Moreover, the scripts also have the ability to exfiltrate data by creating new WebClients objects to upload files to an external address by using the PUT process after determining the location of the target files on the infected system. Read: CISA Warns of Samsung Devices’ Security Flaw, Allowing Android ASLR Bypass