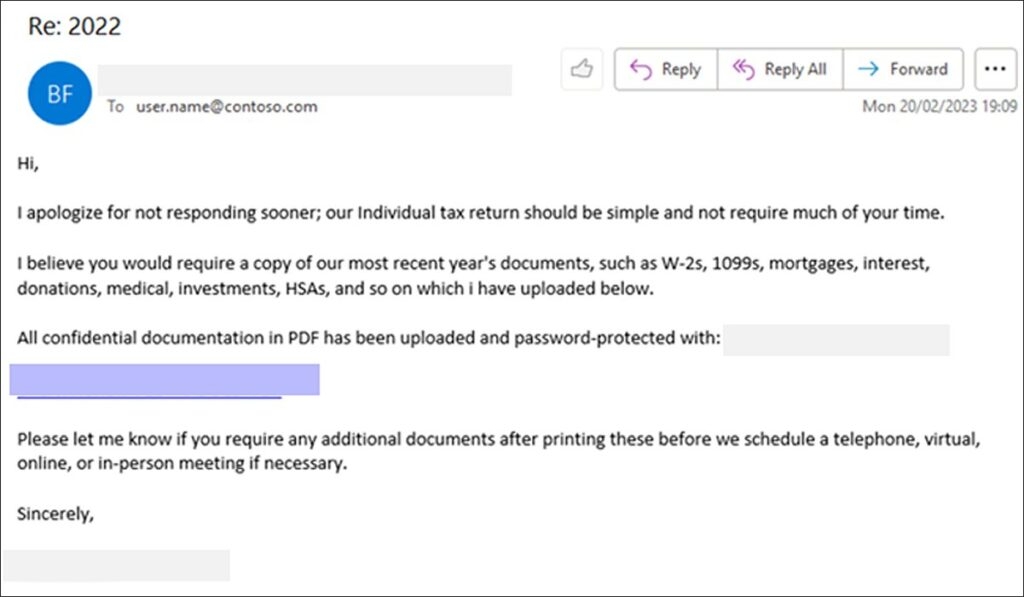
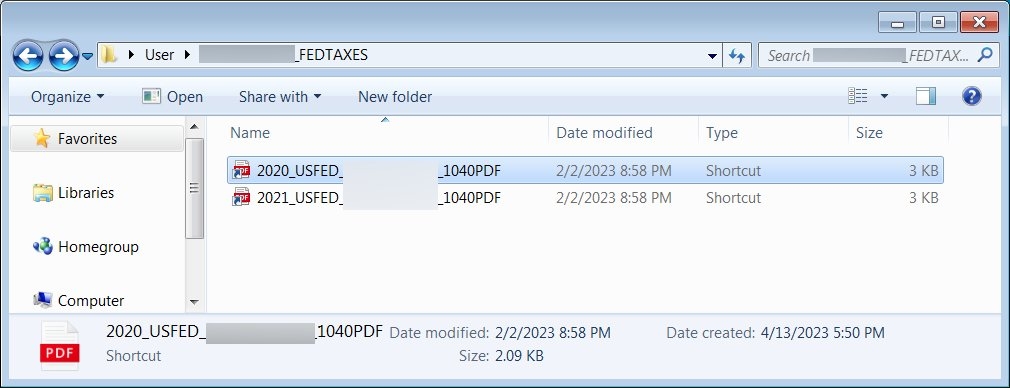
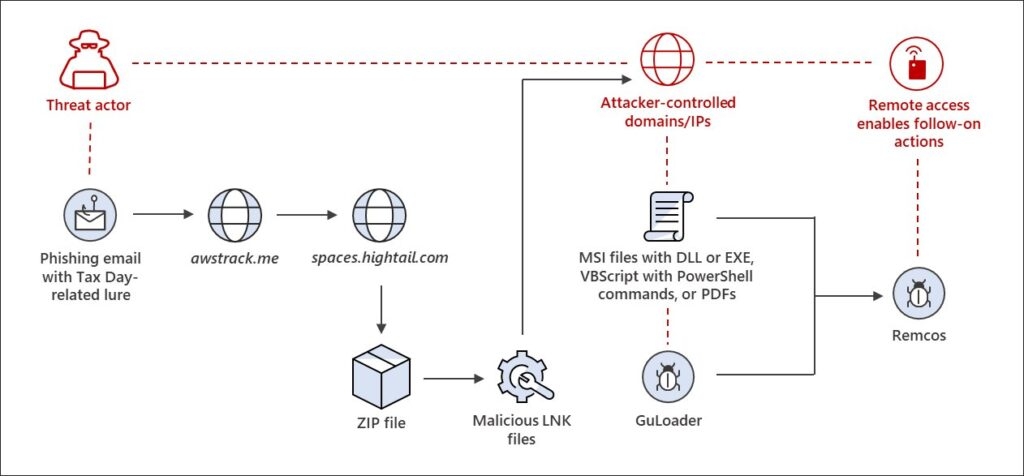
Well, this makes it the perfect time for the threat actors to target the taxpayers, in hope that they will open the malicious files that they could normally be more careful with when they are less occupied. With that being said, Microsoft has been pushing out warnings of the phishing attack, which targets taxpayers and accounting companies with Remote Acess malware that allows threat actors to gain initial access to the corporate network. As the U.S Tax submission day is getting nearer, Microsoft has been pushing out warnings, and the company, in its latest report, mentions that it has observed the comeback of the phishing attacks targeting tax companies & taxpayers to deliver Ramcos Remote Access Trojan (RAT) that infects corporate networks that began this February. Read: Checkpoint Security Researchers Discover Fast Ransomware ‘Rorschach’ with Unique Features Now onto the Phishing attack; the activity starts with emails that pretend themselves as from clients that have sent the required files to complete the tax return. A phishing email that Microsoft saw reads, “I apologise for not responding sooner; our individual tax return should be simple and not require much of your time.” “I believe you would require a copy of our most recent year’s documents such as W-2s, 1099s, interests, mortgages, donations, HSAs, medical investments, and more which I have uploaded below”. These phishing emails have links that users click tracking services to escape being detected by the security software and finally take to a file hosting website that downloads a ZIP file. The Zip archive has a number of files that disguise themselves as PDF files for various tax forums though they are Windows shortcuts. When the target double-clicks them, the Windows shortcut will perform a PowerShell, a heavily obfuscated VBS file from a remote host, which is then saved into C:\Windows\Tasks and executed, and simultaneously the VBS file will download a decoy PDF file to open in it in the Microsoft Edge to keep away to cause suspicion by the targeted person. As per Microsoft, the VBS file will download and execute Guloader malware, installing the Ramcos Remote Access Trojan. Well, Ramcos Remote Trojan is a trojan that threat actors commonly use in phishing attacks to gain initial access. Upon gaining access, the threat attackers spread further through the network to steal data and install other malware on the device. Microsoft says that these phishing activities generally use tax-related themes, although unusually, this campaign only targets individuals & tax firms The initial loader for this activity is malicious files that impersonate PDF files, so a display of file extension is always recommended. Unfortunately, Windows shortcuts are the special file type that uses the link file extension but does not show the file extension. This is what makes it tough to detect the files a file. A shortcut is a disguise that is more difficult. However, listing files in File Explorer in the Details will show the Windows Shortcut, making it easier to detect. Read: Attackers Sending IRS Phishing Emails to Install Emotett Malware