Well, it may sound a little bit strange to some of you, but I have come across numerous Pixel users who straightaway unlock the device’s bootloader as soon as they unbox it. But while all these do tend to add a slew of goodies to your device, but there’s another side to this story that deserves your attention as well. Carrying out these tweaks also comes with its share of downsides. Among them, the most concerning is the SafetyNet getting tripped.
What is SafetyNet and why my Device should Pass it?
For the unaware, SafetyNet is an API that is embedded into your device by Google in order to check if your device has been modified or not. So if your device has been tampered with [rooted], the test will fail and you will not be able to use banking and payments apps or try out games like Pokemon Go. Likewise, Widevine L1 Certification will drop to L3, thereby resulting in your inability to stream DRM content in Full HD.
To make it even more difficult for us to pass this test, Google has switched from the Basic to the Hardware-based Attestation. But by changing the device’s fingerprint to an older Pixel device, you could spoof your device to basic attestation. This in turn will allow you to easily pass the Safetynet and hide root from the desired apps on your rooted Pixel 7/Pro. So without further ado, let’s check out how all of this could be carried out.
How to Pass SafetyNet on Rooted Pixel 7/Pro
Given below are two different methods to get this job done. The first method is the old and lengthier approach but initially, it was our only escape route. However, now there is a new and shorter approach available as well, which we have listed in Method 2 [recommended]. Both these methods should work across numerous Android devices [tested on Pixel 6/7 series and the OnePlus 7 series]. Likewise, it should work on both Android 12 and 13 [should also work on older Android versions, but I haven’t tested them myself]. So on that note, let’s get started. Droidwin and its members wouldn’t be held responsible in case of a thermonuclear war, your alarm doesn’t wake you up, or if anything happens to your device and data by performing the below steps.
METHOD 1: Pass SafetyNet using Magisk Hide Props Config [OLD]
This is the lengthier of the two methods and involves spoofing the device’s fingerprint to one of the older devices that followed Basic Attestation and were easier to bypass.
STEP 1: Install MagiskHide Props Config
STEP 2: Force Basic Attestation
We will now be starting with the implementation of the BASIC attestation on top of the hardware-based so that it becomes easier to bypass. Here’s how it could be done:
STEP 3: Instal Riru Module
Next up, you will have to install the Riru Module, which is a prerequisite for the SafetyNet Fix Module (STEP 5).
STEP 4: Flash SafetyNet Fix
Universal SafetyNet Fix Magisk Module is a module created by XDA Senior Member kdrag0n that completes the process of implementing the BASIC attestation on top of the hardware one. UPDATE: We will now be using the new Safetynet Fix module created by XDA Senior Member displax which works perfectly with Pixel 7/Pro and other devices launched with Android 13 out of the box.
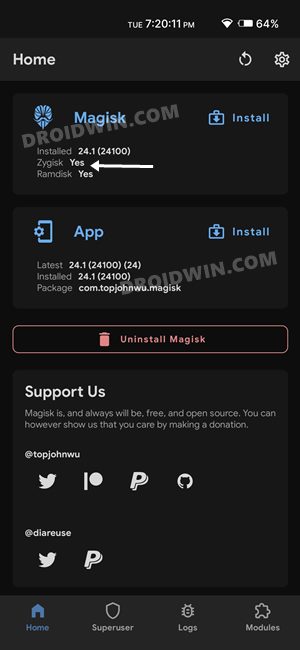
STEP 5: Enforce Deny List and Enable Zygisk
Deny List is the new name for Magisk Hide. For the unaware, it is the feature through which you could hide root from various installed apps onto your device. So let’s first enable this Deny List and then configure it according to the requirement.
STEP 6: Configure DenyList
STEP 7: Hide Magisk App
STEP 8: Delete Play Service and Play Store Data
STEP 9: Check SafetyNet Results on Pixel 7/Pro
Now that we are done with all the hard work, let’s check out the associated rewards. Do note that Magisk has now removed the option to check SafetyNet. So you will now have to take the help of a third-party app. As for this guide, we will be using the YASNAC – Yet Another SafetyNet Attestation Checker. That’s it. These were the steps to pass the SafetyNet Test and hide root from apps on your rooted Pixel 7/Pro using Magisk Hide Props Config. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
METHOD 2: Pass SafetyNet without Magisk Hide Props Config [NEW]
The shorter of the two methods, this doesn’t require you to spoof the device’s fingerprint or flash the Magisk Hide Props Config, all thanks to tweaks made by the developer of the Universal SafetyNet Fix Module. So on that note, let’s get started with the steps to pass Safetynet on your rooted Pixel 7/Pro.
STEP 1: Hide Magisk App
STEP 2: Enable Systemless Hosts
STEP 3: Enable Zygisk
STEP 4: Configure Denylist
Denylist is the new name for the traditional Magisk hide. You could use this functionality to hide root from the desired apps, apart from the three compulsory apps listed below.
STEP 5: Flash Universal SafetyNet Fix Module
STEP 6: Delete Data
You will now have to delete the app data of all the apps from which you have hidden root. These include the compulsory Google apps and the desired apps of your choice.
STEP 7: Check SafetyNet Test Results
That’s it. these were the steps to pass SafetyNet on your rooted Pixel 7/Pro. If you have any queries concerning the aforementioned steps, do let us know in the comments. We will get back to you with a solution at the earliest.
How to Pass SafetyNet test after installing Xposed or EdXposedFix Magisk Safetynet API Error: Detailed GuideHow to Fix ctsProfile Mismatch Error on Rooted AndroidBootloop after installing/updating Magisk: How to Fix
About Chief Editor
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()
![]()